The military use of radar has always had a yin-yang dynamic – as new forms of radar are developed, so too are new ways to jam them. A team of physicists at the University of Rochester has discovered how to defeat the latest active radar jamming methods by taking advantage of the quantum properties of photons. While this new anti-jamming technology cannot remove the false information, it provides an immediate alert that false information is being received.
The new jamming method on the block is Digital Radio Frequency Memory (DRFM) jamming. DRFM works by intercepting the radar signal, modifying the signal by introducing false information about the target, than retransmitting the modified signal toward the radar. In principle, the radar cannot distinguish the altered signal from a legitimate target signal because the altered signal contains all the signatures and fingerprints of the original radar beam. The class of DRFM jamming methods is sufficiently broad and flexible that constructing effective countermeasures to the jamming using conventional technology is extremely difficult.
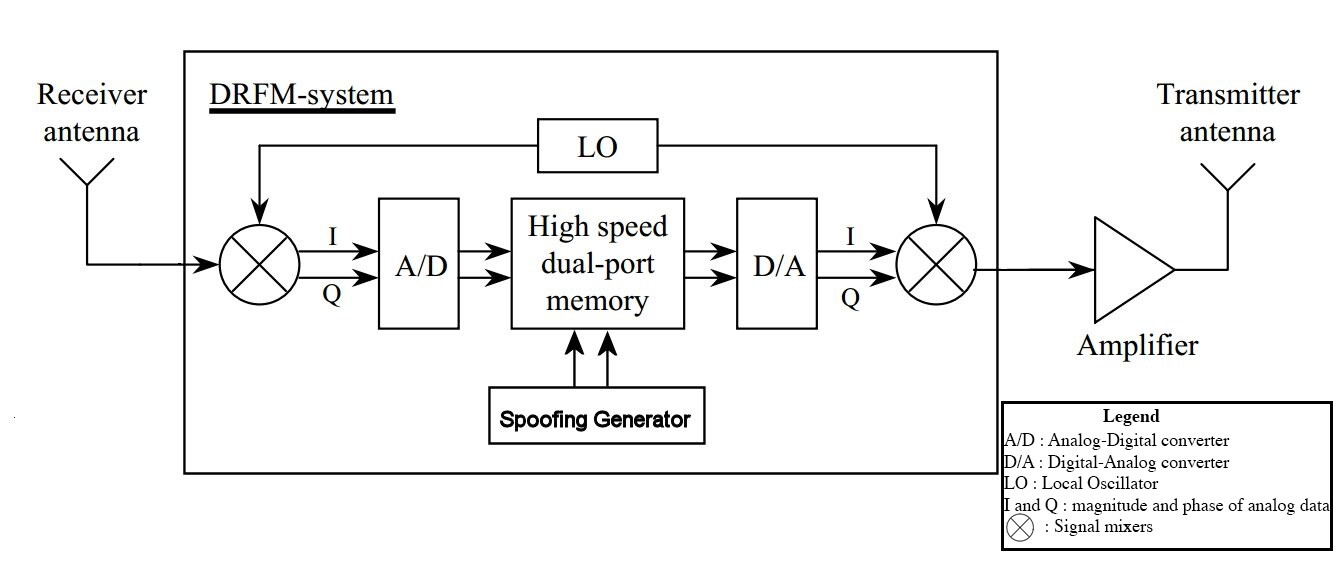
Physicists at the University of Rochester have now discovered a way to use the quantum properties of photons to create the first imaging system that cannot be fooled by DRFM jamming. The result is an amazingly simple real-time protocol for detecting DRFM spoofing.
The key is to use polarization of the radar signal as a quantum signature. A radio or light wave is described by a polarization angle, defined as the direction along which the electric field of the wave is oriented. A polarizer is an optical element that allows only radiation sharing its polarization direction to pass through unscathed. If the same wave is directed through a polarizer misaligned by 90 degrees, no signal passes through.
When the polarization direction of a photon and a polarizer are misaligned by an angle other than 90 degrees, some of the photon passes through. However, that photon now has the polarization of the polarizer – not the polarization direction of the original photon. This seems a bit odd, but is the quantum phenomenon at the foundation of the new anti-jamming protocol.
Taking a leaf out of the team's research paper, we'll use the antics of a couple of fearless quantum adventurers named Bob and Alice to illustrate the technology. Alice is running the radar, and sends out a radar beam in which the photons are vertically polarized. In a simple illustration, she receives the signal reflected from a target through a second vertical polarizer. If Alice decides to look at the incoming signal with a horizontal polarizer, the vertically polarized signal will be completely blocked, and she won't see the radar return.
Now put Bob on the target with a DRFM jamming system. Bob has a DRFM jammer, and uses it to spoof the returned signal. Alice will then see whatever Bob wants her to see, instead of the actual radar returns. But with a simple test, Alice immediately knows that Bob has been playing games.
How? The problem Bob runs into is that it isn't possible to measure the direction of polarization of a photon. Bob detects the incoming radar beam with a receiver which at best detects a particular polarization direction. If he chooses a polarization different from Alice's, the misaligned polarization of his antenna works like a pair of polarized sunglasses, and lets only part of the signal through. However, this isn't the problem, as there is plenty of signal for Bob to work with.
The problem shows up when Bob retransmits the altered signal back to Alice. Given the information Bob knows (and doesn't know) about the incoming signal, the best he can do is retransmit the signal with the polarization of his detecting antenna. This means there will be some angle of polarization shift that Bob cannot know, and thus cannot correct.
When Alice receives the signal, she sees the altered signal that Bob intends for her to see. However, when she changes her receiver to look at horizontal polarization, Alice will still see Bob's altered image because of the polarization shift. Alice knows she wouldn't see her own reflected signals in horizontal polarization, so someone (and from long association she suspects Bob) has altered the signal.
The actual process isn't quite as direct as described above, but this is the gist of the protocol, which is a modification of the physics underlying quantum key distribution. When the interception of a signal changes the quantum properties of the signal, the sender can detect the interception. According to Mehul Malik, first author on the paper reporting these results, “In order to jam our imaging system, the object must disturb the delicate quantum state of the imaging photons, thus introducing statistical errors that reveal its activity.”
Malik and his co-workers have tested their anti-jamming protocol by bouncing photons off an airplane-shaped target and measuring the polarization error rate in the return signal. Without any eavesdropping the system easily imaged the airplane. However, when the return signal was spoofed by DRFM jamming, they saw the image of a bird, but the jamming was easy to spot.
The process isn't completely reliable, mainly because radar is not a collection of single-photon processes. There are lots of photons in the radar beam, which in a simple protocol all have the same polarization. Bob in principle can use part of the radar signal to determine its polarization (which can be done using a large number of photons), and then use that knowledge when retransmitting the spoofed signal.
However, this is difficult to do because of the time delays in determining the radar beam polarization, and can easily be countered by, for example, changing the radar polarization rapidly, sending out the radar beam on a number of frequencies, and having different polarizations on each, or a combination of both. The point is that the new anti-jamming protocol pushes all the effort of the radar game away from the radar site, and back onto the target, for whom spoofing the radar signal has just become a far more difficult process.
Source: ArXiv.org (PDF) via MIT Technology Review






